Compatibility View is the most common backward compatible solution in Internet Explorer, it can be configured by Compatibility View Settings, Group Policy and Local intranet security zone. We can control some of the sub-domains to be displayed in Compatibility View and some of them not by using these configurations.
Compatibility View Overview
In Compatibility View:
- The User-Agent string that Internet Explorer sends to the server contains "MSIE 7.0" token to declare itself as Internet Explorer 7.
- When choosing the default document mode, Internet Explorer will simulate IE7's behavior. It will use IE7 document mode if the page contains a <!DOCTYPE> declaration, otherwise it will use IE5 Quirks document mode.
You can read: IE11 Migration Guide: Understanding Browser Mode, Document Mode, User-Agent and X-UA-Compatible for more information.
Configure Compatibility View
Following are all the possibilities to make a website being displayed in Compatibility View.
- Compatibility View settings.
- Microsoft compatibility lists.
- Internet Explorer group policy Compatibility View settings.
- Local intranet.
Compatibility View settings
You can manually add a domain to Compatibility View list from Tools > Compatibility View settings. This setting only accepts top level domain, the list shows "microsoft.com" even if you typed "store.microsoft.com".
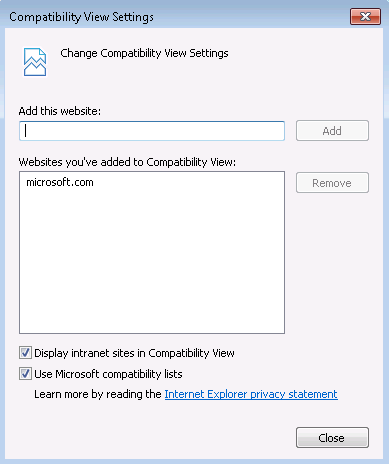
As shown in the image above, all webpages from "microsoft.com" will be displayed in Compatibility View after adding "microsoft.com" to the list.
Microsoft compatibility lists
Microsoft compatibility lists are XML files on "microsoft.com", Microsoft updates these lists monthly. The XML file contains a lot of Internet sites that needs to be displayed in older browser mode, IE parses the list and use the specified browser mode to display the website. IT administrator doesn't need to care much about these lists because enterprise internal websites are not included. If you are the owner or the developer of a public website and wish to remove your site from Microsoft compatibility lists, you can refer to following two articles.
Group Policy
You can enable following group policy settings to make a website being displayed in Compatibility View.
Administrative Templates > Windows Components > Internet Explorer > Compatibility View: Use Policy List of Internet Explorer 7 sites
There is another group policy setting under same category: Use Policy List of Quirks Mode sites, the difference between this setting and Compatibility View is: For website in Use Policy List of Quirks Mode sites, IE always uses IE5 Quirks document mode to render the webpage no matter the webpage contains a <!DOCTYPE> declaration or not unless the page specifies a document mode via an X-UA-Compatible value.
It should be noted that the two settings above accept sub-domains only on IE9 and above. If you added "store.microsoft.com" to the list, IE8 just ignores it.
Local Intranet Zone
Local intranet site is displayed in Compatibility View by default. You can turn it off by deselecting Tools > Compatibility View settings: Display intranet sites in Compatibility View.
And therefore, we can let a website be displayed in Compatibility View by making it as a local intranet site. Besides adding a website to the Local Intranet Zone manually, Internet Explorer also detects intranet site automatically based on some rules.
Adding site to Local Intranet Zone
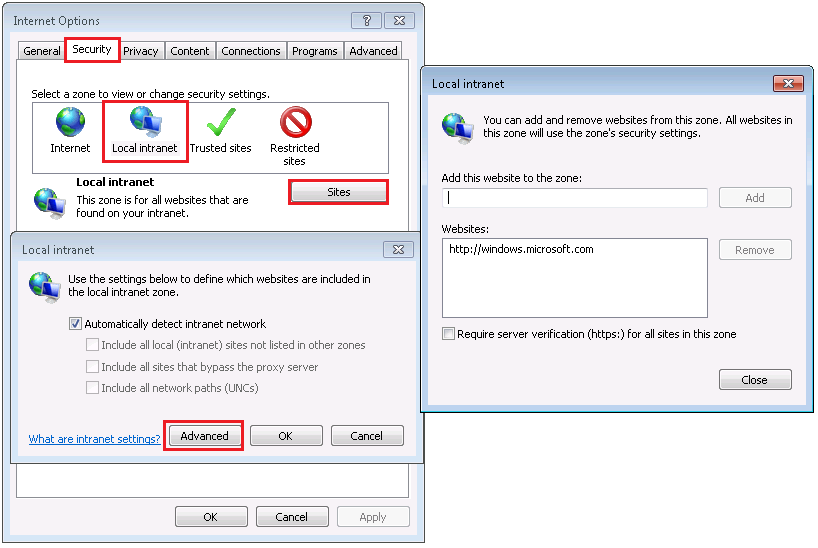
You can add a website to Local Intranet Zone through Tools > Internet Options > Security > Local intranet > Sites > Advanced.
Group Policy
You can add a website to Local Intranet Zone by enabling following group policy setting.
Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page: Site to Zone Assignment List
This policy setting allows you to manage a list of sites that you want to associate with a particular security zone.
- 1: Local Intranet Zone
- 2: Trusted Sites Zone
- 3: Internet zone
- 4: Restricted Sites Zone
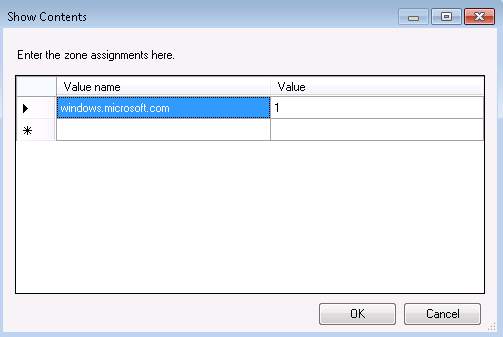
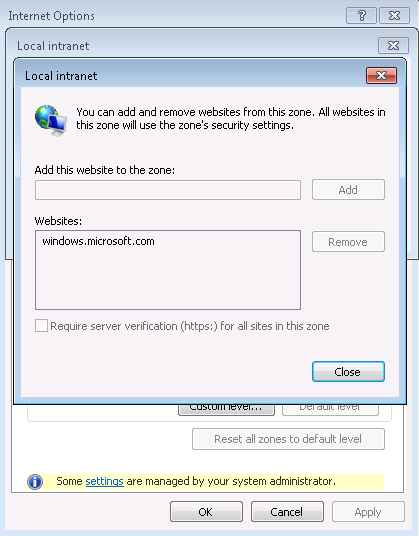
For example, you can add "windows.microsoft.com" to Local Intranet Zone by assigning value: "1" as shown in the image below.
After enabling Site to Zone Assignment List, it will overwrite user's own site-to-zone assignment which was configured manually from IE GUI setting page and the user will not be able to manage the list by him or herself. As shown in the image below, the user can only view the list, but the Add and Remove buttons are disabled.
Automatic detection
Besides the two methods above, IE also follows the four rules below to automatically detect whether a website belongs to Local Intranet Zone.
The PlainHostName rule (aka "The Dot rule"). If the URI's hostname doesn't contain any periods (e.g. http://mysite/) then it is mapped to the Local Intranet Zone.。
The fixed Proxy Bypass list. If the user has a fixed proxy specified inside Tools > Internet Options > Connections > LAN Settings, then sites listed to bypass that proxy will be mapped to the Local Intranet Zone.
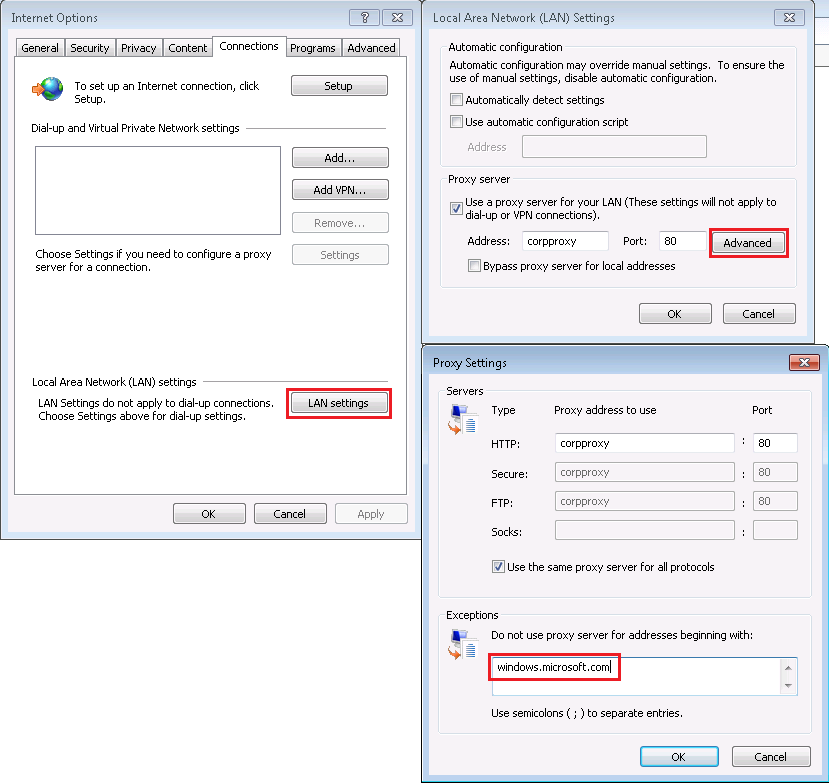
As shown in the image above, the user has a fixed proxy server: corpproxy:80, however "windows.microsoft.com" is listed in the bypass list. In this case, "windows.microsoft.com" will be recognized as a Local Intranet site.
(WPAD) Proxy Script. If the user's proxy configuration is Automatically detect settings or Use automatic configuration script inside Tools > Internet Options > Connections > LAN Settings, the browser will run the
FindProxyForUrlfunction in the specified WPAD proxy configuration script to determine which proxy should be used for each request. If the script returns "DIRECT", the browser will bypass the proxy and the site will be mapped into the Local Intranet Zonefunction FindProxyForURL(url, host) { if (url.indexOf('azure.microsoft.com') > -1) { return 'DIRECT'; } else { return 'PROXY corpproxy:80'; } }For example, if IE is configured to use the proxy script above, then "azure.microsoft.com" will be recognized as a Local Intranet site.
Network paths (UNCs). If the URL is a network UNC path (e.g. \\tsclient\c\www\index.html) then it is mapped to the Local Intranet Zone.
The four rules above can be enabled or disabled by the three settings inside Tools > Internet Options > Security > Local Intranet > Sites.
- Include all local (intranet) sites not listed in other zones. This setting controls the first rule.
- Include all sites that bypass the proxy server. This setting controls the second and third rules.
- Include all network paths (UNCs). This setting controls the fourth rule.
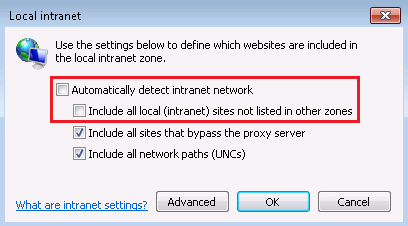
Automatic detection only works on a domain-joined computer. For a non-domain-joined computer, http://localhost will not be mapped to Local Intranet Zone. If you want a non-domain-joined computer to apply these automatic detection rules, you need to deselect the setting Automatically detect intranet network and manually select the rules you want to apply.
FAQ
Why a Trusted site is displayed in Compatibility View?
There are four possibilities for a trusted site is displayed in Compatibility View.
- The user added the website to Compatibility View list.
- IT administrator added the website to IE group policy Compatibility View settings.
- Microsoft compatibility list contains this website.
- The website meets any of the automatic detection rules.
It is easy to rule out the first three possibilities and ignore the fourth. Assuming that the you added http://localhost to Trusted Site Zone on a domain-joined computer, in this case, http://localhost is still displayed in Compatibility View because it meets the automatic intranet detection rule (the URI's hostname doesn't contain any periods). If you want to make http://localhost not being displayed in Compatibility View, you can consider following options.
Disable Display intranet sites in Compatibility View inside Tools -> Compatibility View settings.
Disable Automatically detect intranet network and the rule which applies to the website inside Tools -> Internet Options > Security > Local intranet > Sites.
How to make a sub-domain not being displayed in Compatibility View while the other sub-domains need to be display in Compatibility View?
Assuming that most sub-domains of "contoso.com" need to be displayed in Compatibility View, but only one sub-domain "new.contoso.com" doesn't work in Compatibility View and needs to be displayed without Compatibility View. Following are two common solutions.
- Add the top-level domain "contoso.com" to Local Intranet Zone so that all sub-domains will be displayed in Compatibility View. After that add "new.contoso.com" to Trusted Sites zone so that it will be recognized as Trusted site and not displayed in Compatibility View.
- Add X-UA-Compatible meta tag or HTTP response header to the pages of "new.contoso.com" to specify a correct document mode for rendering the page. Hence the website will be displayed in correct document mode event if it is displayed in Compatibility View.